The official title of the standard is
«Information technology— Security techniques — Information security management systems Requirements».
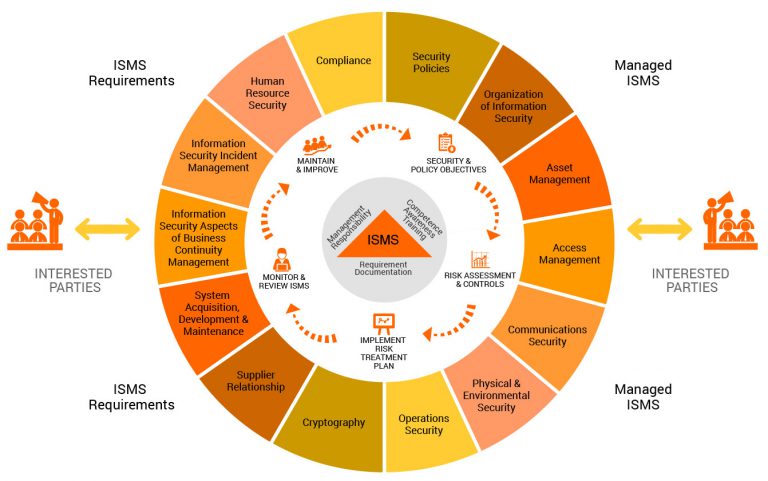
27001:2013 has ten short clauses, plus a long annex, which cover:
Con Cert Quality Management GmbH guarantees an accredited certification, giving to Organizations the suitable passport for International market, ensuring with accuracy and independency the principles and rules established by the standard ISO 27001:2013.
The ISO/IEC 27001 Information Security Management standard helps organizations to keep their information assets secure, by building an information infrastructure against the risks of loss, damage or any other threat.
Companies that certify their management system against ISO/IEC 27001 validate that the security of financial information, intellectual property, employee details, or information entrusted from third parties is being successfully managed and continually improved in accordance with widely accepted best practices and the standard’s framework.
ISO/IEC 27001 Introduction training course enables you to become familiar with the basic concepts of an Information Security Management System (ISMS).
By attending the ISO/IEC 27001 Introduction training course, you will understand the importance of ISMS and the benefits that businesses, society and governments can obtain.
ISO/IEC 27001 Foundation training allows you to learn the basic elements to implement and manage an Information Security Management System as specified in ISO/IEC 27001. During this training course, you will be able to understand the different modules of ISMS, including ISMS policy, procedures, performance measurements, management commitment, internal audit, management review and continual improvement.
ISO/IEC 27001 Lead Implementer training enables you to develop the necessary expertise to support an organization in establishing, implementing, managing and maintaining an Information Security Management System (ISMS) based on ISO/IEC 27001. During this training course, you will also gain a thorough understanding of the best practices of Information Security Management Systems to secure the organization`s sensitive information and improve the overall performance and effectiveness.
ISO/IEC 27001 Lead Auditor training enables you to develop the necessary expertise to perform an Information Security Management System (ISMS) audit by applying widely recognized audit principles, procedures and techniques. During this training course, you will acquire the necessary knowledge and skills to plan and carry out internal and external audits in compliance with ISO 19011 and ISO/IEC 17021-1 certification process